Initial deployment
Create a new virtual machine
- Navigate to Create a virtual machine in Azure.
- Name your machine and select the latest Ubuntu Server as the image. Choose a size with at least 2 CPUs and 8 GB of RAM. Other settings can be left as default.
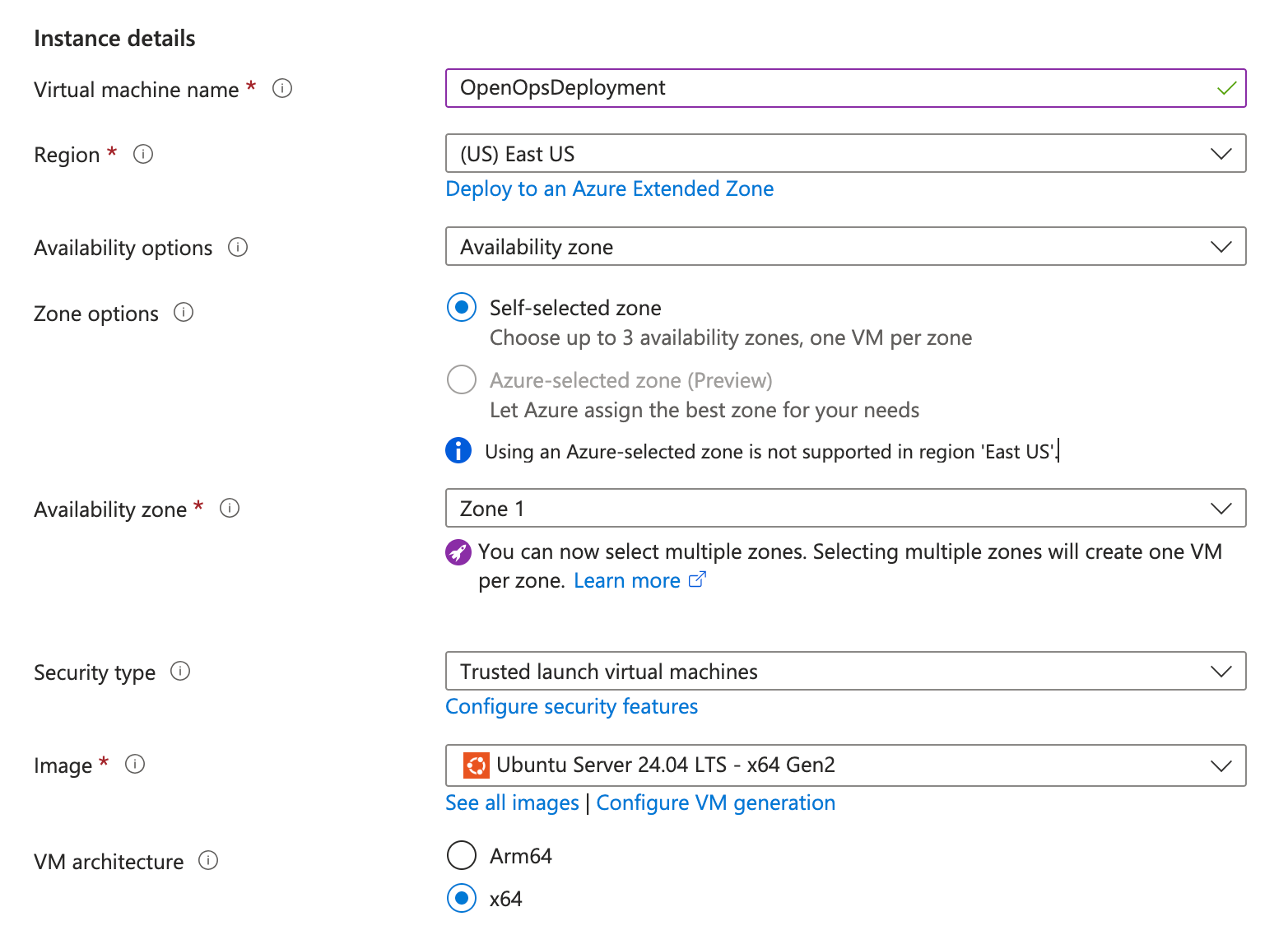
- Click Review + create at the bottom, then Create to create the machine. You will be asked to download the private key.
- Once the VM deployment is complete, click Go to resource.
- From the deployment overview, navigate to Networking > Network settings.
- Under Rules, click Create port rule, then select Inbound port rule:
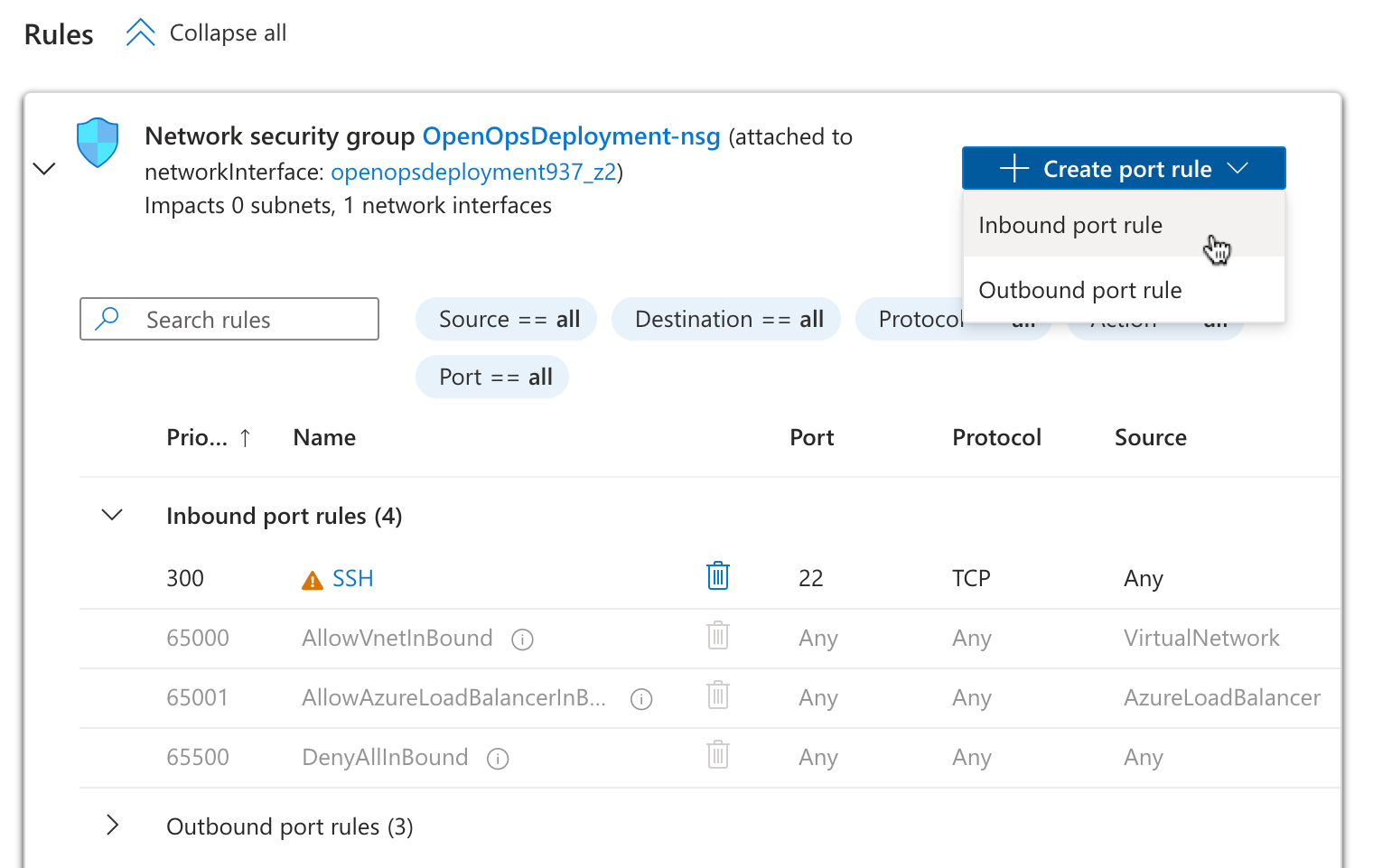
- In security rule settings:
- Enter
80in the Destination port ranges text field. - Using the Source dropdown, choose to open the port to everyone (default), to your personal IP address only, or to a preferred range.
- Enter a name for the rule in the Name text field.
- Click Add to create the rule.
- Enter
Connect to the virtual machine with Cloud Shell
- From the VM deployment overview, open the Overview tab, then click Connect and select Connect:
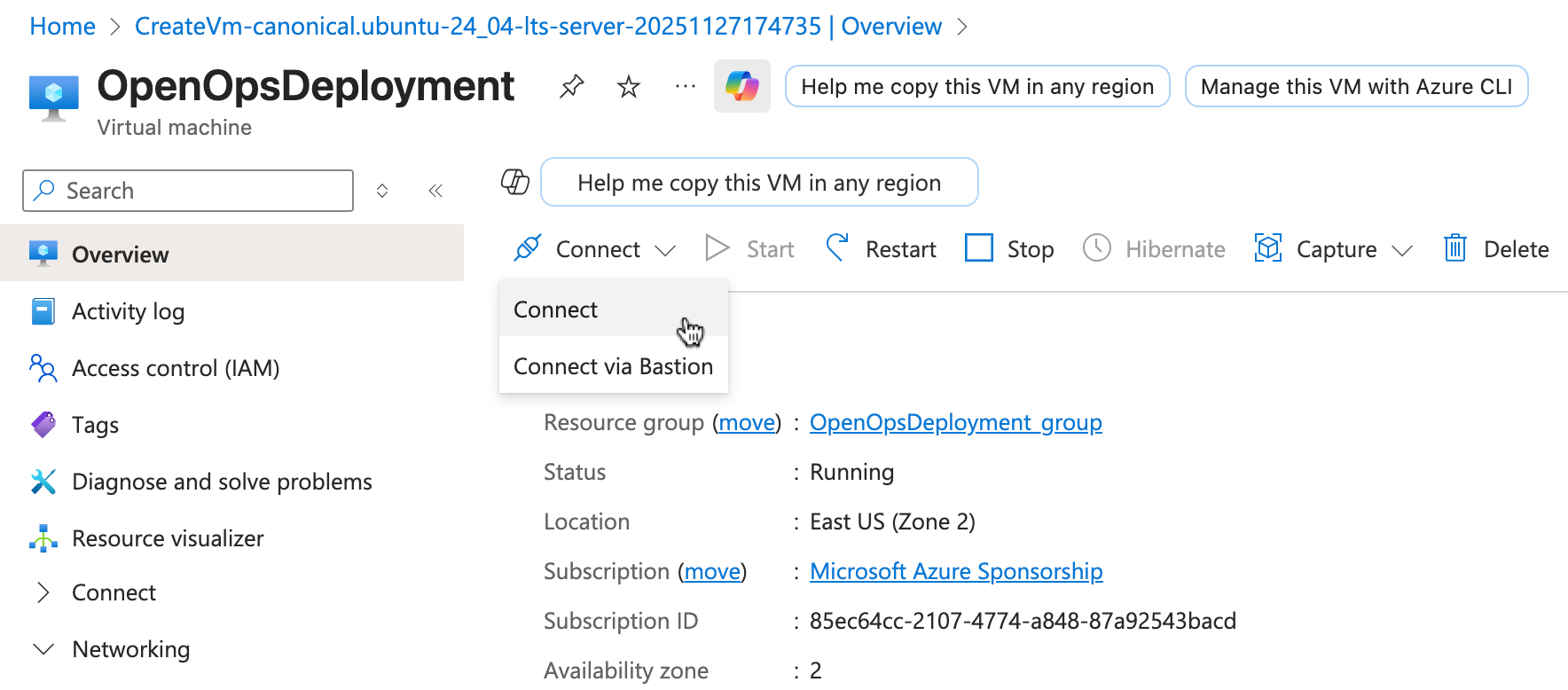
- In the Connect view, expand More ways to connect. In the SSH using Azure CLI section, click Connect via Azure CLI:
- In the SSH using Azure CLI overlay, click Configure + check access. Once the access check is complete, click Connect.
- Choose Bash as the shell type. This will open Cloud Shell inside the Azure Portal.
Install OpenOps
Run the following command in your terminal to install, update, configure and run OpenOps:http://20.20.20.20).
Network ports used by OpenOps
By default, OpenOps does not require any inbound ports other than the application port80.
The following ports are used by bundled services and, in most cases, should not be exposed:
5432: The PostgreSQL database used by OpenOps. Expose this port only if you need direct database access, such as for connecting OpenOps to external analytics tools. Restrict access to a VPN or a trusted IP range.6379: OpenOps’ internal Redis service. Expose this port only if required for debugging or monitoring purposes. Restrict access to a VPN or a trusted IP range.
Getting credentials for Azure connections
See this guide.External databases
To use external PostgreSQL or Redis databases, modify the relevant variables in the.env file. You can disable the corresponding containers by adding a profile in the docker-compose.yml file:
db profile in .env or in Docker Compose, that container won’t start.
After making any changes to the .env file, restart the OpenOps containers:
Enabling TLS
For production usage, it’s recommended to enable TLS (HTTPS). In addition to the security aspect, this also ensures that workflow templates load properly in all browsers.Automatically
The easiest way to enable TLS is to use an OpenOps script that requests and sets up a TLS certificate from Let’s Encrypt. Before running the script, make sure you have a domain name that points to your ‘s external IP address. If you’re configuring DNS right before running the script, you may need to wait for the DNS change to propagate.- Run the following command in your terminal:
- When prompted, enter a domain name that points to the external IP address of your .
- When prompted, enter an email address to receive certificate-related notifications from Let’s Encrypt.
Manually
Alternatively, you can create a TLS certificate yourself. This lets you use DNS validation from Let’s Encrypt (rather than the HTTP validation the automatic script performs) or request a certificate from a different provider. To set up TLS manually:- Obtain certificate and private key files from your certificate provider.
- Upload the certificate files to your OpenOps installation under the
tlsdirectory:<OpenOps installation path>/tls/cert.pem(certificate file)<OpenOps installation path>/tls/key.pem(private key file)
- Open the
.envfile in your OpenOps installation directory and update the following variables:- Set
OPS_NGINX_CONFIG_FILEtonginx.gateway.tls.conf - Set
OPS_PUBLIC_URLto the secure URL of your OpenOps installation (e.g.https://openops.example.com)
- Set
.env file, restart the OpenOps containers:
Disabling host validation
By default, OpenOps does not allow workflows to call internal network addresses such as127.0.0.1 or 192.168.0.0. This affects HTTP and SMTP actions, as well as webhook triggers. Host validation protects users from creating workflows that could accidentally or maliciously access internal services, scan networks, or escalate privileges.
You may need to disable this check in certain circumstances, such as in non-production deployments or when workflows intentionally interact with internal-only infrastructure.
To disable host validation, open the .env file in your installation folder and set the OPS_ENABLE_HOST_VALIDATION environment variable to false.
After making any changes to the .env file, restart the OpenOps containers:
Configuring allowed SMTP ports
By default, OpenOps allows SMTP connections on ports 25, 465, 587, and 2525. Administrators can customize which SMTP ports are available by setting theOPS_SMTP_ALLOWED_PORTS environment variable in the .env file.
To configure allowed SMTP ports, open the .env file in your installation folder and set the OPS_SMTP_ALLOWED_PORTS variable to a comma-separated list of port numbers:
Port numbers must be valid TCP ports in the range 1-65535. At least one valid port must be configured. Invalid port numbers will be filtered out.
.env file, restart the OpenOps containers:

